41 secure network diagram
May 4, 2016 - The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons. It will help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics, Network Plans for secure wireless network, Computer Security Diagrams to share knowledge about effective ways of networks ... The typical architectural diagram shown below offers only two slim layers of protection, yet it is widely accepted that more layers equal a more secure environment. In the diagram below, an attacker must compromise only one server to gain access to the Web applications provided on the same system. Additionally, the basic Web-based network architecture does not protect against application attacks (e.g. buffer overflows or injections), since its primary source of protection are network firewalls. As application attacks gain in popularity, network-based firewalls will be insufficient to effectively prevent attacks from this new threat. While some network firewalls have application firewall capabilities, most security experts consider these underpowered offerings less protective than the single-purpose application firewalls that are available. In fact, network firewalls cannot protect custom Web applications at all. Another issue basic implementations have is their default use of well-k...
• Defining Secure Network Architecture - What is a secure network architecture - Why a secure network architecture - Who needs a secure network architecture • Designing Secure Network Architecture - Defense in depth - Layers of security - Security levels - ZdCditMdlZone and Conduit Models - Building Blocks • Questions ...

Secure network diagram
Network Security Diagrams Solution in ConceptDraw STORE. Each Network Security Diagram example included to Network Security Diagrams Solution is well thought-out and designed by professionals with a goal to demonstrate the exceptional drawing capabilities of ConceptDraw DIAGRAM software. Besides each example is an ideal start for your own ... A truly secure network design allows you to effectively manage your client networks with a layered security approach. Read on to learn more about designing truly secure networks. ... You might not chart physical security on a technical diagram, but physical security policy needs to be as specific as possible and communicated broadly ... Different types of network diagrams include network switch diagrams, computer network diagrams, and network security diagrams. Each of these network diagrams focuses on a single component or aspect of a network. Logical Network Diagrams. A logical network diagram addresses how information passes through a network.
Secure network diagram. Secure hybrid network. 10/04/2021. R. P. N. Browse code. This sample deploys a hub and spoke network, a mock on-premises network, and connects both with a site-to-site VPN connection. Where applicable, each resource is configured to send diagnostics to an Azure Log Analytics instance. For detailed information, see the Implement a secure hybrid ... The goal of the VPN server is not to make transmissions end-to-end secure; the goal is to provide a secure connection from the computer off-campus back to campus, so that traffic traversing the Internet on it's way to campus is secure. This permits off-campus users to access resources on the campus network without revealing sensitive data such ... Learn how to set up a small business network with one server. Tips for network design and where to pay special attention. Plus, network diagram, router, switch, and firewall recommendation. For more help building office network call Microsoft certified network specialist at 858 769 5393. The above network diagram is an example of home network using subnets. subnet 1: This is the most important sub-network to protect. Devices and computers here are used to store your most important data and perform your most important online activities. Any potential risky activities should be avoided in this sub-network.
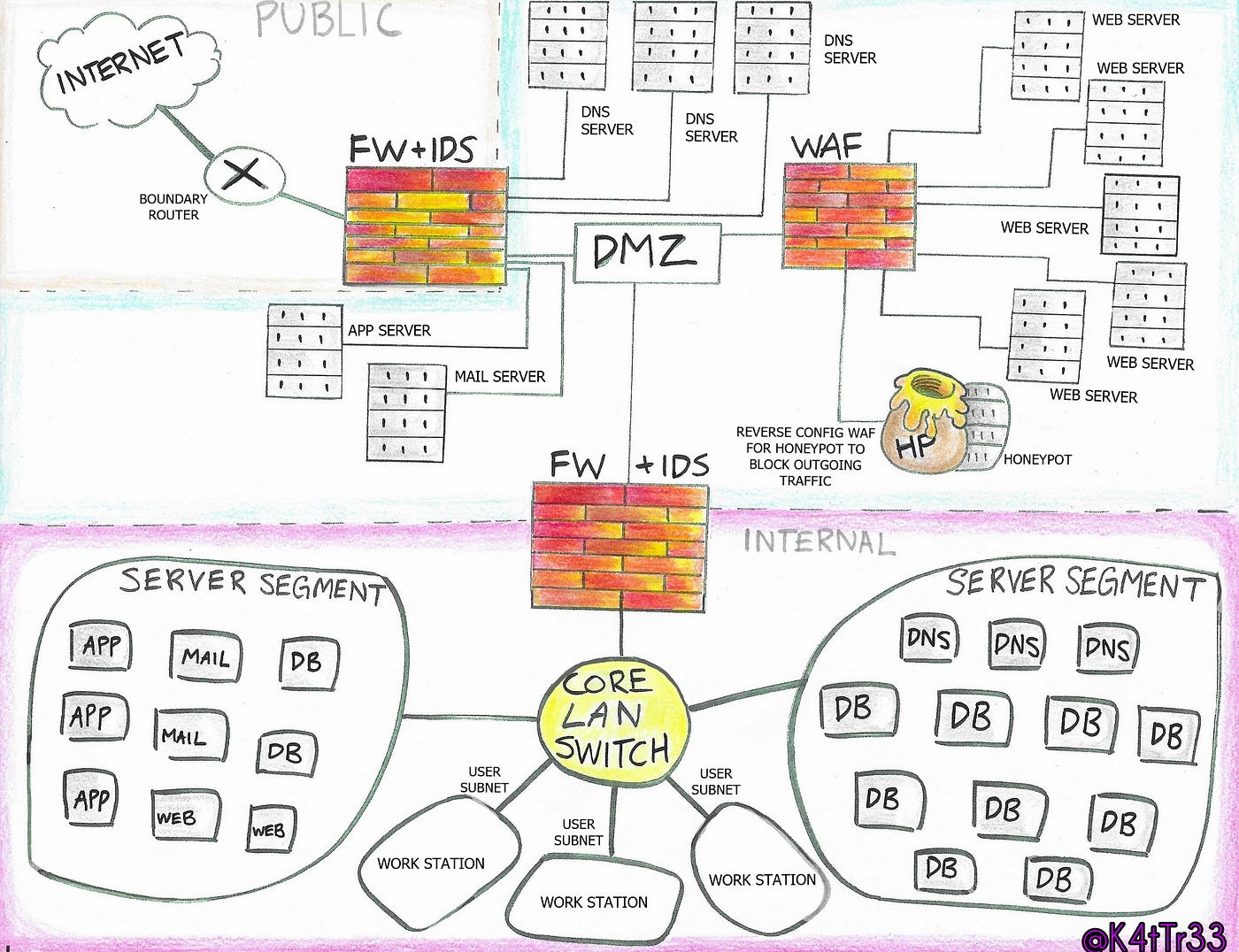
Security by far is one of the most important aspects of any organization. A network security diagram helps the user map out the methods and processes that must be followed to create the security protocols. With a correct and effective method, a network security diagram can be created that shows what valuable information can be processed and stored. Network Security Diagram Template. Draw Network Diagram with Visual Paradigm Online (VP Online), a web-based Network Diagram maker. The Network Diagram editor has tailor-designed features that ease the editing of chart. Edit this Template. Segment your network footprint and create secure communication paths between segments. Align the network segmentation with overall enterprise segmentation strategy. Design security controls that identify and allow or deny traffic, access requests, and application communication between segments. Protect all public endpoints with Azure Front Door ... MSCIA C700 - Secure Network Design Paper. Secure Network Design. As noted previously, I have experience with WGU in the BSIT program and I'd like to help increase the information about the MSCIA program as I go along. For the love of Pete don't do what I did on this one and panic, fret, and overall procrastinate for more than a month.
Network Security Architecture Diagram. Network security is the set of actions adopted for prevention and monitoring the unauthorized access, ensuring information security and defense from the attacks, protection from misuses and modification of a network and its resources.. Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions ... A network diagram is a visual representation of a computer or telecommunications network. It shows the components that make up a network and how they interact, including routers, devices, hubs, firewalls, etc. This network diagram shows a local area network (LAN): Depending on its scope and purpose, a network diagram may contain lots of detail ... 14 pages. C700 Ip address and subnetting.docx. Western Governors University. Secure Network Design - C700. COMPUTER S C700 - Fall 2019. Register Now. C700 Ip address and subnetting.docx. 42 pages. report-69085855-c00e-4009-8d2d-b41f4ef5238e.pdf. If you were to ask network architects and engineers about their favorite part of the job, I doubt any of them will respond with "creating and maintaining network diagrams." It's not the most glamorous task—yet requirements 1.1.2 and 1.1.3 of the Payment Card Industry Data Security Standard (PCI DSS), along with general good security hygiene, render it a necessary one.

Figure 2 1 From Cyber Security Network Anomaly Detection And Visualization Major Qualifying Project Semantic Scholar
basic network security diagram ( Network Diagram) Use Creately's easy online diagram editor to edit this diagram, collaborate with others and export results to multiple image formats. We were unable to load the diagram. You can edit this template on Creately's Visual Workspace to get started quickly. Adapt it to suit your needs by changing ...
Network diagrams can become quite complex, but building them doesn't have to be when you use Lucidchart. Whether you're a responsible employee documenting your system for troubleshooting down the road or demonstrating security compliance (we'll assume you're always a responsible employee), you can get started in seconds with one of the network diagram templates below.
Securing a Platform for the Network Diagram. To eliminate the complication of creating documentation, especially for small business network setup diagrams, it is important to find a program that will efficiently assist you in streamlining the process of creating a network diagram.
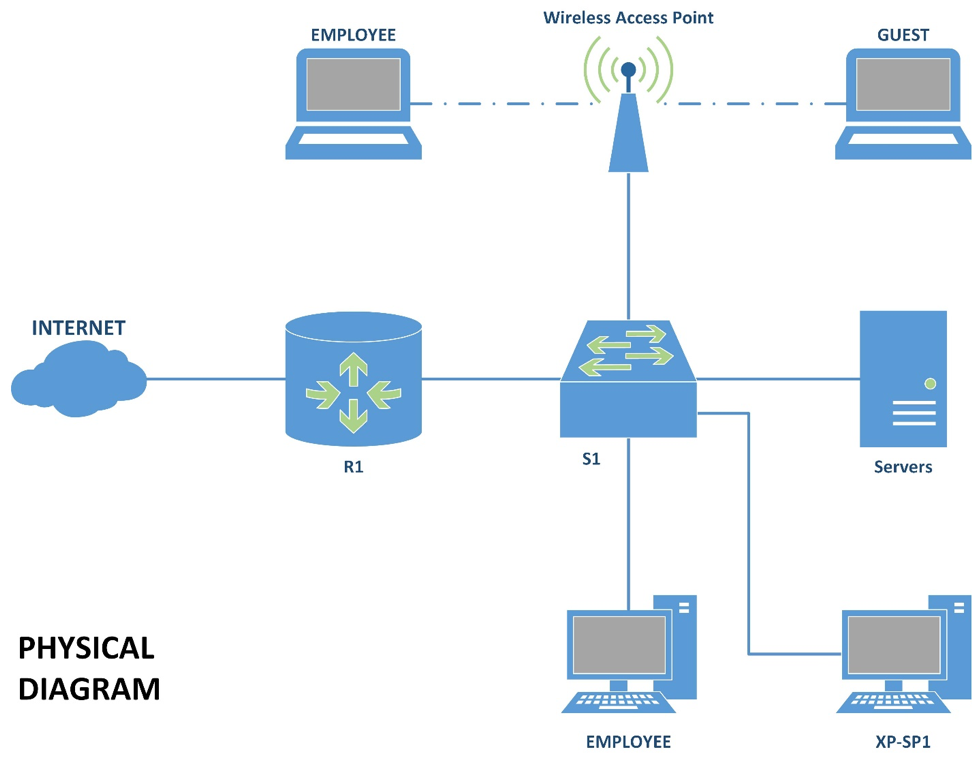
The diagram has a purpose for both the networking and cybersecurity teams to secure the wireless network and remove the errors as the wireless networks are more vulnerable to cyber-attacks. The diagram is also crucial for modifying the networks, extending them, or making a whole new one.
A network diagram will help organizations and teams visualize how devices like computers, and networks like telecommunications, work together. Network diagrams help paint a picture of how these operational networks function and they identify components like routers, firewalls and devices, and visually show how they intersect. This blueprint acts as a road map to allow […]
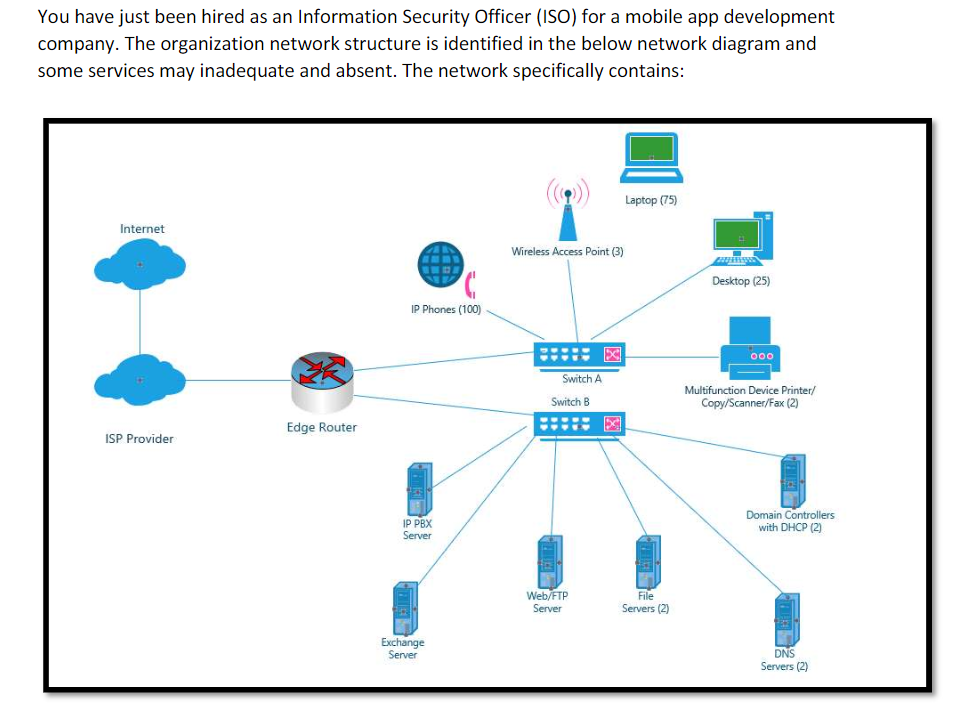
nstructions You will design a secure network. You will do this by drawing a logical network diagram using the tool of your choice (it can even be hand drawn). You will need to show 2 separate gigabit WAN interfaces for redundancy and bandwidth aggregation purposes. You will need to show a dual wan router/firewall (no WiFi built in), 3 separate ...
Your network diagram can focus on the security of your network, specific devices, or the physical or logical aspects of your network. Now that you know what network diagrams are, you can learn about the different ways to create your own network diagrams—manually, automatically, or semi-automatically. Manual Network Diagramming Software
May 21, 2020 · Katrina K. May 21, 2020 · 5 min read. Learning to Diagram a Secure Network. How I learned to diagram a secure network and not WAN a cry! Unedited image retrieved from VPS Net. After learning ...
Fundamentals of Computer Network Security Specializationcourse 4 Secure Networked System with Firewall and IDSModule 1 - Secure Network DefenseIn this module...
Nov 25, 2020 · In short: Are there any example/use case/reference 'secure' network diagrams, such as the one on the left above, that have been released from a well-known source? EDIT: All of the answers are great, thank you for taking the time to answer! I am struggling to accept one because they both provide really good perspective on the matter.
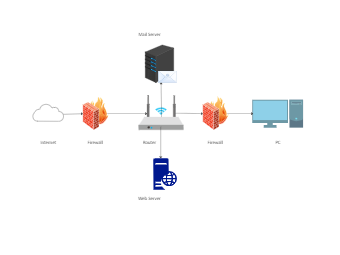
Network communications between the SSH server and the target server are NOT encrypted by the SSH tunnel (see diagram below), so if the servers are running on different machines, ideally they should be located together on a secure network.
The Best Free Network Diagram software - Easy-to-Use, Powerful and Web-Based. Fast Network Diagram tool to draw Network Diagram rapidly and easily. Also support Flowchart, BPMN, UML, ArchiMate, Mind Map and a large collection of diagrams. FREE for non commercial use! Start Free now.
Different types of network diagrams include network switch diagrams, computer network diagrams, and network security diagrams. Each of these network diagrams focuses on a single component or aspect of a network. Logical Network Diagrams. A logical network diagram addresses how information passes through a network.
A truly secure network design allows you to effectively manage your client networks with a layered security approach. Read on to learn more about designing truly secure networks. ... You might not chart physical security on a technical diagram, but physical security policy needs to be as specific as possible and communicated broadly ...
Network Security Diagrams Solution in ConceptDraw STORE. Each Network Security Diagram example included to Network Security Diagrams Solution is well thought-out and designed by professionals with a goal to demonstrate the exceptional drawing capabilities of ConceptDraw DIAGRAM software. Besides each example is an ideal start for your own ...
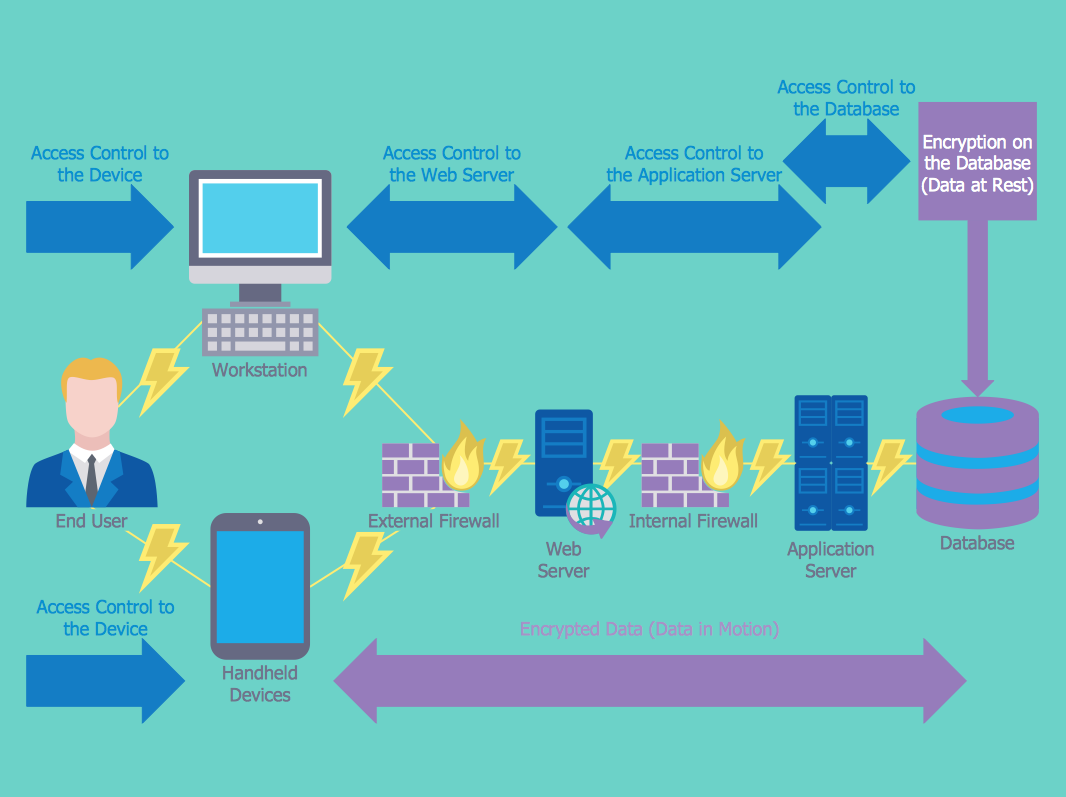
How To Create A Network Security Diagram Network Security Diagrams Computer Network Architecture Computer And Network Examples Secure Network Architecture Diagram

Network Fun A Security Network Engineer S Blog Network Diagrams Created In Ms Paint Vs Ms Visio What Is Your Preference
Cyber Security Cwins Research Lab Cybersecurity And Wireless Networking Innovations Lab Prof Danda B Rawat


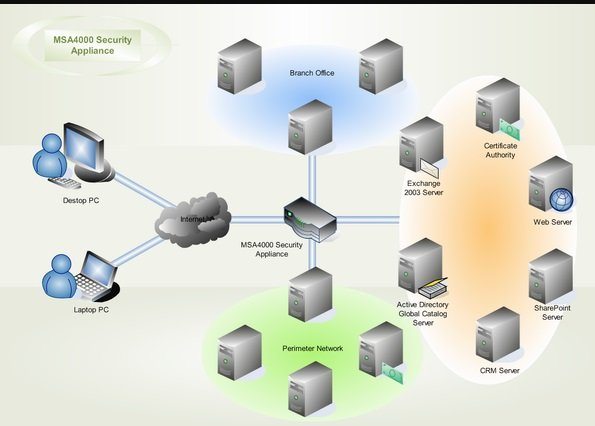

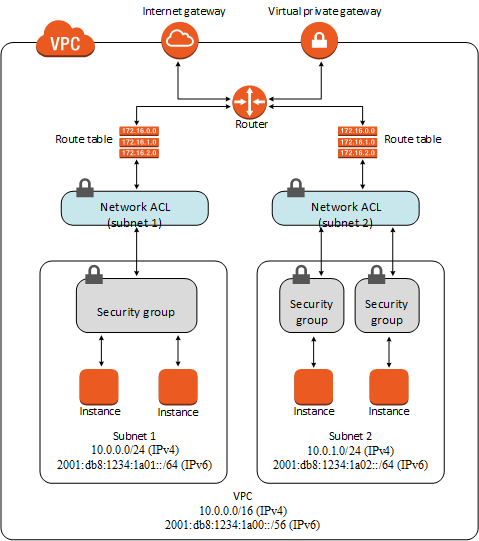
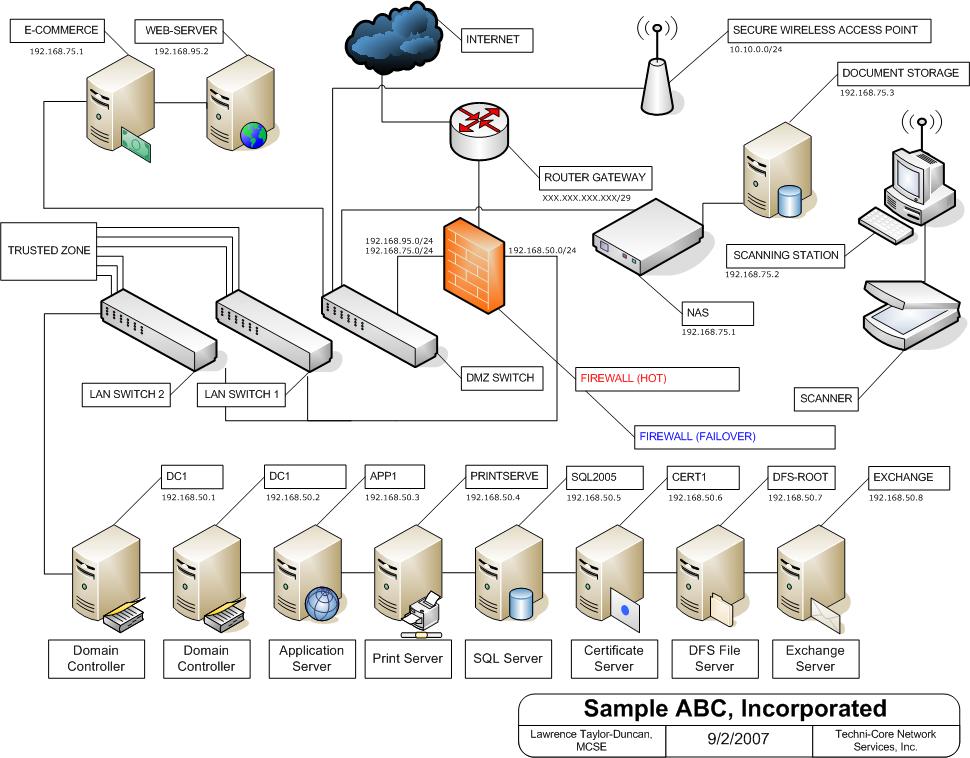











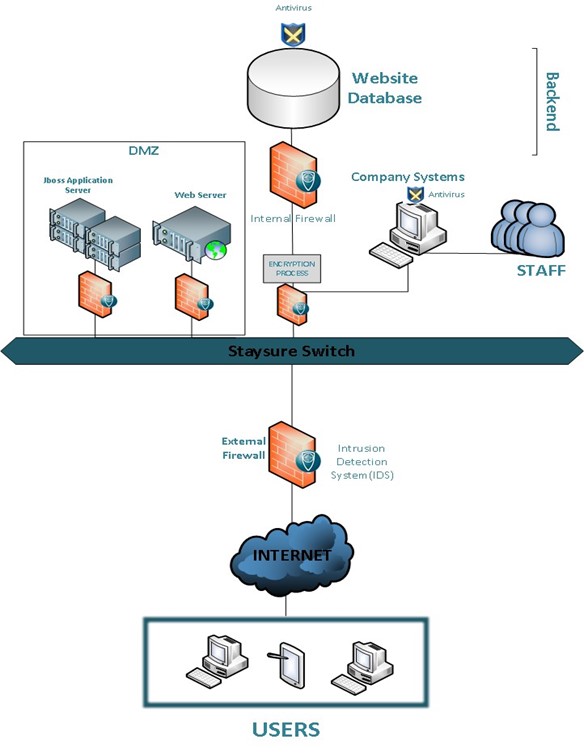







Comments
Post a Comment